Blog
By Shivam Dharpure
•
March 20, 2025
In India, law enforcement made significant strides, sentencing a FedEx scammer to six years in prison, arresting a Hyderabad fraudster linked to a ₹55 lakh ‘digital arrest’ scam, and busting a scam centre trafficking 549 Indians to Southeast Asia. Meanwhile, a 75-year-old woman lost ₹75 lakh to fraudsters posing as CBI officers, while a Navi Mumbai IT manager was duped into a ₹7 lakh insurance scam. In response, the government partnered with WhatsApp under ‘Scam Se Bacho’ to combat cyber frauds more effectively.
On the international front, Google is in talks to acquire cybersecurity firm Wiz for $33 billion, a move aimed at enhancing cloud security against Microsoft and Amazon. Additionally, NTT DATA and CrowdStrike have expanded their AI-powered cyber resilience partnership, using advanced threat intelligence to combat stealthier cyber threats.
By Shivam Dharpure
•
February 16, 2025
In India, authorities arrested 14 cybercriminals in Nuh for running online scams, while 11 individuals in Ahmedabad were caught opening fake bank accounts using fraudulent Aadhaar IDs. The Jamtara cyber gang has expanded operations across multiple states, making detection harder for law enforcement. Maharashtra Cyber Cell launched a crackdown on concert ticket black marketing, enforcing stricter identity verification measures on BookMyShow and Zomato. Meanwhile, 73 officers have been selected for the Cyber Commando program, enhancing India’s cyber defence capabilities.
On the international front, former UK cyber spy chief Sir Jeremy Fleming called for more transparency in intelligence operations amid rising concerns over cyber surveillance. The 5th Annual Global Cyber Innovation Summit, known as the “Davos of Cybersecurity”, brought together top security experts to discuss AI-driven cyber threats and national defence strategies.
By Shivam Dharpure
•
February 15, 2025
🔎 Visionary Vigilance: Episode 18 Summary
🚔 India’s cybercrime police have intensified their actions, arresting 12 cyber gang members linked to Cambodia, while West Bengal and Odisha police nabbed fraudsters running investment scams. The Punjab & Haryana HC has demanded a detailed report on cybercrime complaint mechanisms, emphasizing greater accountability in tackling online frauds. 🔍💼
🏦 RBI has launched new banking domains (bank.in & fin.in) to prevent phishing scams and enhance financial security. Meanwhile, Madhya Pradesh introduced ‘Nagar Suraksha Cyber Samiti’ to educate citizens about cyber threats. 📊
⚔️ On the global front, the UK is fast-tracking “cyber warriors”, restructuring military training to focus on cyber defence operations. The British military has even eliminated traditional basic training to expedite recruitment for cybersecurity roles. 💻🇬🇧
By Shivam Dharpure
•
February 14, 2025
Episode 17 brings critical insights into rising cyber frauds, financial scams, and international cyber threats. 🚨💻
In India, cyber frauds have jumped by 900% in four years, with small cities like Deoghar, Nuh, and Mathura emerging as scam hubs. The Delhi Police dismantled a cyber fraud network, while Tamil Nadu lost ₹1,700 crore to cybercrimes in 2024. A PIL in Bombay HC seeks better cybersecurity for Maharashtra government websites, and Bengaluru Police arrested seven cybercriminals linked to VoIP scams. The Union Budget 2025 allocated ₹1,900 crore to strengthen India’s cybersecurity defenses. 🔐📊
Internationally, DeepSeek AI suffered a major cyber attack, exposing sensitive backend data and user logs and raising alarms about AI-driven cyber threats. The US and Dutch authorities dismantled a Pakistan-based cybercrime network, while global cybersecurity agencies issued new security guidelines to protect network edge devices from hacking threats. 🌍⚠️
By Shivam Dharpure
•
February 13, 2025
Episode 16 brings major cyber fraud crackdowns, financial scams, and global cybersecurity threats. 🚔💻
In India, the Hyderabad Police arrested 52 cybercriminals, including four bank officials, linked to frauds worth ₹88.32 crore. Meanwhile, Pune residents lost ₹2 crore to online scams, and a 75-year-old airline retiree was digitally arrested and scammed of ₹1 crore. The CBI announced an international cybercrime crackdown, aiming to dismantle fraudulent operations worldwide. 🚨
Fraudsters are also impersonating senior citizens to steal money through hacked WhatsApp accounts, and fake cybercrime complaint websites are charging victims for reporting fraud. In Rajasthan, police arrested a ₹2,000 crore scam mastermind, uncovering a massive fake investment network.
On the global front, the EU sanctioned Russian hackers for cyberattacks on Estonia’s government, while a U.S. crackdown shut down 39 cybercrime websites selling hacking tools.
By Shivam Dharpure
•
February 12, 2025
Episode 15 highlights major cybercrime busts, financial frauds, AI security threats, and global cybersecurity interventions. 🚔💻
In India, the UP STF arrested the mastermind behind a ₹4,900 crore ‘digital arrest’ scam, while 67 Indians trafficked to cyber scam centers in Laos were rescued. The Hyderabad Cyber Crime Unit recovered ₹21.9 lakh for scam victims, and Faridabad Police arrested 41 cybercriminals involved in fraudulent investments and phishing schemes. Meanwhile, the ED arrested two masterminds in Kolkata and Delhi for laundering cyber fraud money through crypto transactions. Jharkhand Police cracked down on Jamtara’s ₹10 crore fraud network, targeting fake call center scams. 🚨💰
On the global front, China and Southeast Asian nations dismantled cyber slavery camps, exposing forced scam labor. The DeepSeek AI chatbot suffered a cyber attack after becoming the most-downloaded app, highlighting vulnerabilities in AI security. Additionally, the MintsLoader malware campaign infected corporate networks
By Shivam Dharpure
•
February 2, 2025
Episode 14 of Visionary Vigilance uncovers alarming cyber frauds, international cyber threats, AI-driven scams, and major law enforcement crackdowns. 🌍🔐
🔴 National Cybercrime Updates
• Gorakhpur Police dismantles ₹70 crore cyber fraud ring with 30 arrests, revealing a large-scale betting and financial scam. 🚔💰
• 15 cybercriminals in Nuh busted for sextortion and financial fraud, using fake social media accounts and extortion tactics. 📱⚠️
• Tiruppur-based fraudsters arrested for arranging money mule bank accounts, facilitating financial crimes across India. 💳🚨
• Puducherry Cybercrime Police cracks down on predatory loan apps, exposing digital extortion networks targeting vulnerable borrowers. 💰📲
• Hyderabad businessman loses ₹28 lakh in a fake Boeing stock scam, highlighting the rise in investment frauds via Telegram groups. 📉💀
• ICICI Bank faces a potential data breach, with the BASHE ransomware group claiming access to confidential customer data. 🔓🏦
By Shivam Dharpure
•
February 1, 2025
Visionary Vigilance: Cybersecurity Digest – Ep. 13 Welcome to Episode 13 of Visionary Vigilance , your weekly deep dive into cyber threats, law enforcement actions, and global security updates . This edition covers 17 major cyber frauds, law enforcement crackdowns, and emerging cyber threats , underscoring the growing importance of digital awareness and cyber hygiene . 🌍🔐
By Shivam Dharpure
•
January 31, 2025
Episode 12 highlights major cybersecurity incidents, from multi-crore scams and AI-driven frauds to global cyber warfare.
🔴 National Cyber Updates:
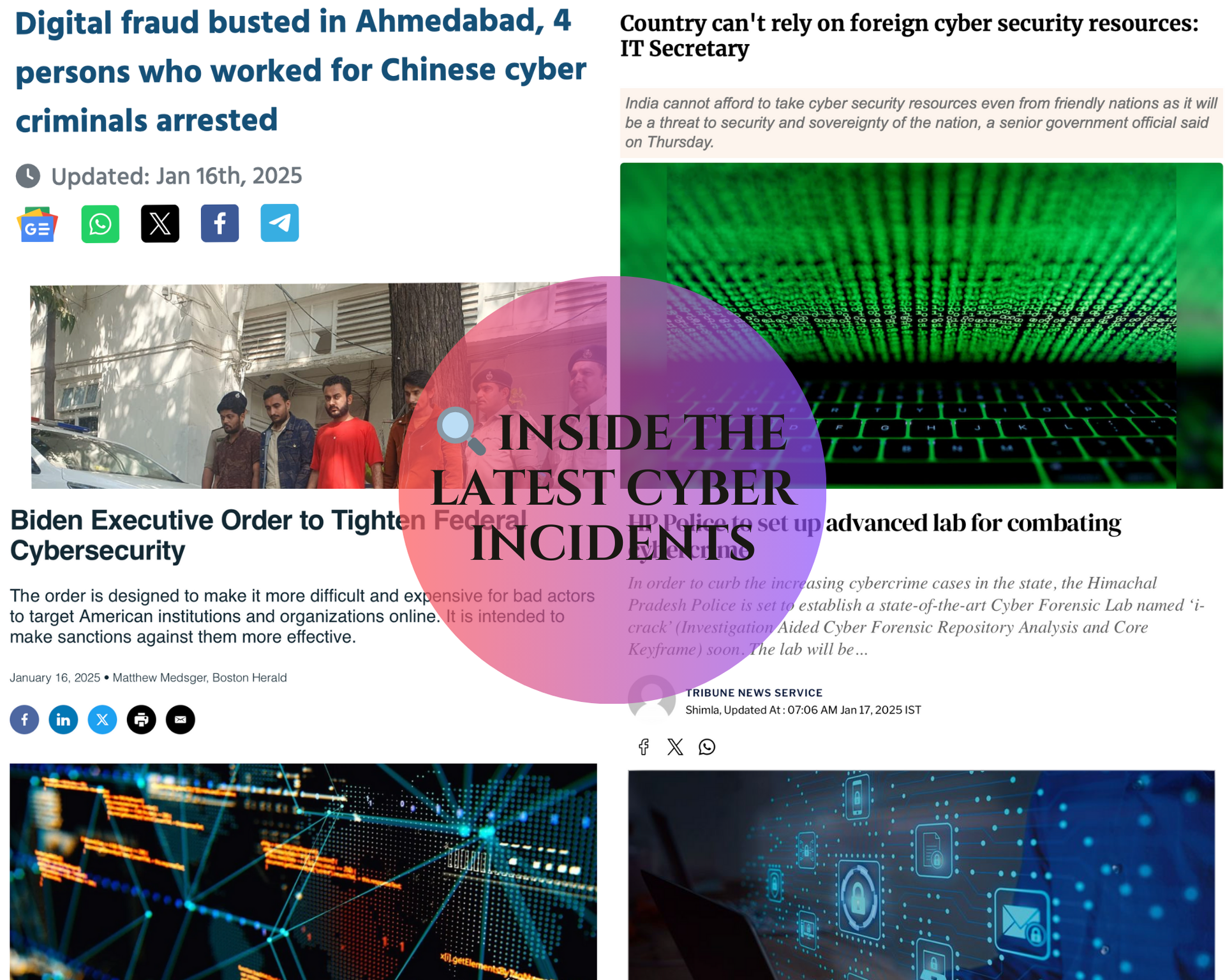
• Ahmedabad cyber scam busted, linked to Chinese fraudsters 💰🇨🇳.
• Jammu Cyber Cell recovers ₹6.9 lakh from online scams 💻🔄.
• Pune police arrest 3 for ₹67.69 lakh fraud targeting job seekers 🚨🏦.
• Bhopal residents feared trapped in cyber slavery abroad 🏴☠️.
• Maharashtra police prevent ₹98 crore fraud through swift action 🚔.
• Punjab establishes a Security Operations Centre (SOC) for cyber defense 🏛️🔐.
• India’s IT Secretary calls for local cybersecurity innovation, reducing foreign dependence 🇮🇳💡.
🌍 International Cyber Threats:
• North Korea linked to ₹1,960 crore WazirX crypto heist 💻💰.
• US Treasury Secretary’s computer hacked by Chinese cyber spies 🇺🇸🕵️♂️.
• Russia’s Star Blizzard hackers target WhatsApp users 📲🇷🇺.
• FBI remotely wipes PlugX malware from US & European PCs 🔥💻.
By Shivam Dharpure
•
January 30, 2025
Episode 11 of Visionary Vigilance uncovers 17 major cybersecurity incidents spanning India and the global stage, showcasing sophisticated cyber frauds, government interventions, and law enforcement crackdowns.
• 🔴 National Highlights:
• ₹2 crore mobile smuggling racket dismantled in Delhi 📱💰.
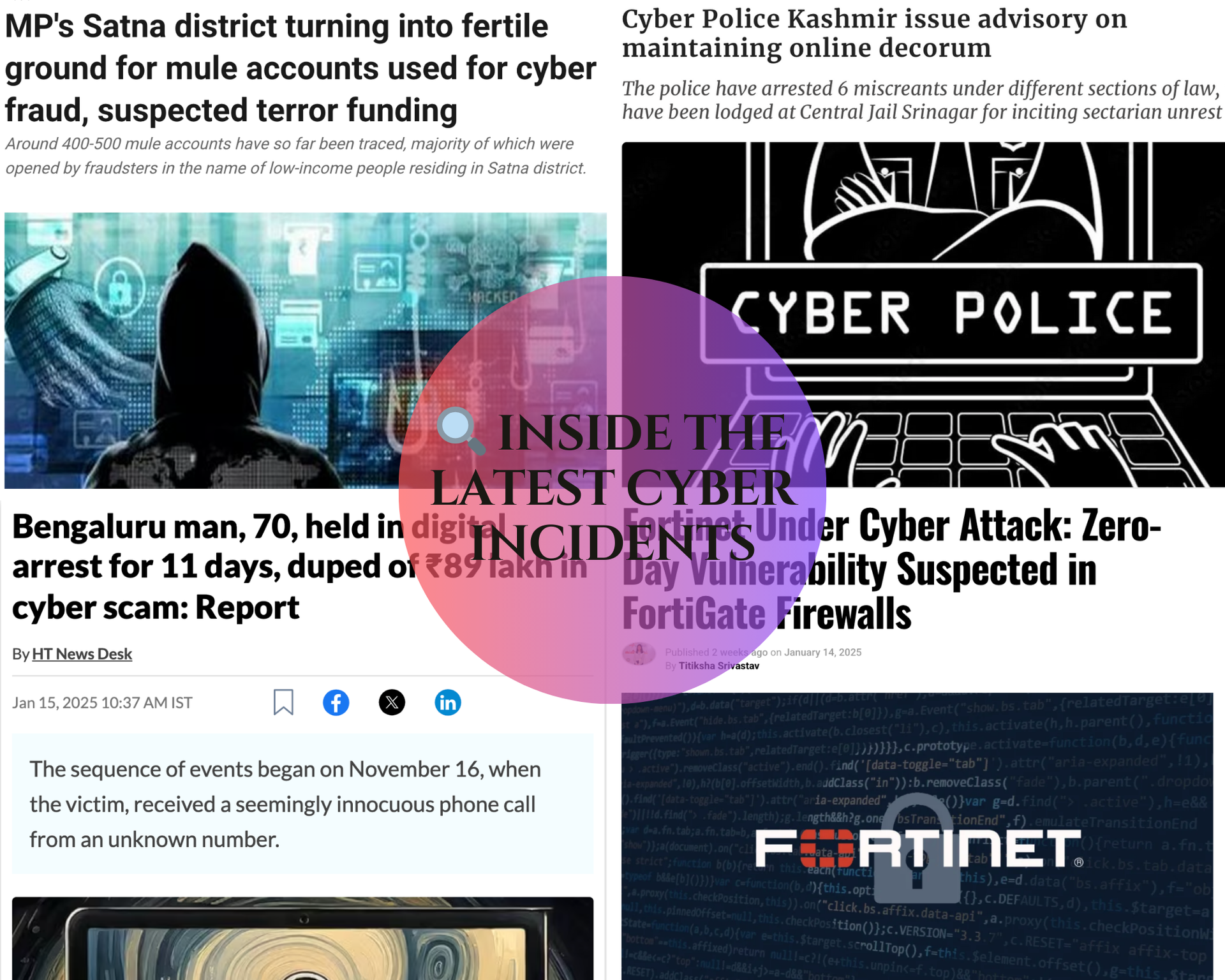
• Indore woman loses ₹1.6 crore in a Laos-linked “digital arrest” scam 🚨.
• ₹31 lakh stolen from three victims through health card, insurance, and job scams 🏦💻.
• Ludhiana seniors lose ₹28 lakh in fake pension schemes 🎖️👴🏻.
• MHA rolls out new cybercrime policies to fortify digital safety across states 🏛️💡.
• ₹1,800 crore saved as India’s cybercrime registry blocks 6 lakh fraudulent transactions 🚔💳.
• UP police rescue a doctor from a hotel-based “digital arrest” scam 🏥⚠️.
• 🌍 International Cyber Threats:
• North Korea linked to ₹1,960 crore WazirX hack, with funds suspected to finance missile programs 🚀💰.
• Three Russians charged for running crypto-mixing services tied to ransomware money laun
+919691568071
Ambazari, Basti Verma Layout Road, Sudam Nagar, Nagpur
Maharashtra, 440033
[email protected]
www.thevisionarybose.com
All Rights Reserved | Visionary Bose Pvt Ltd
© 2025



